测试Apk
dida.apk
情景再现
测试抓包环境.
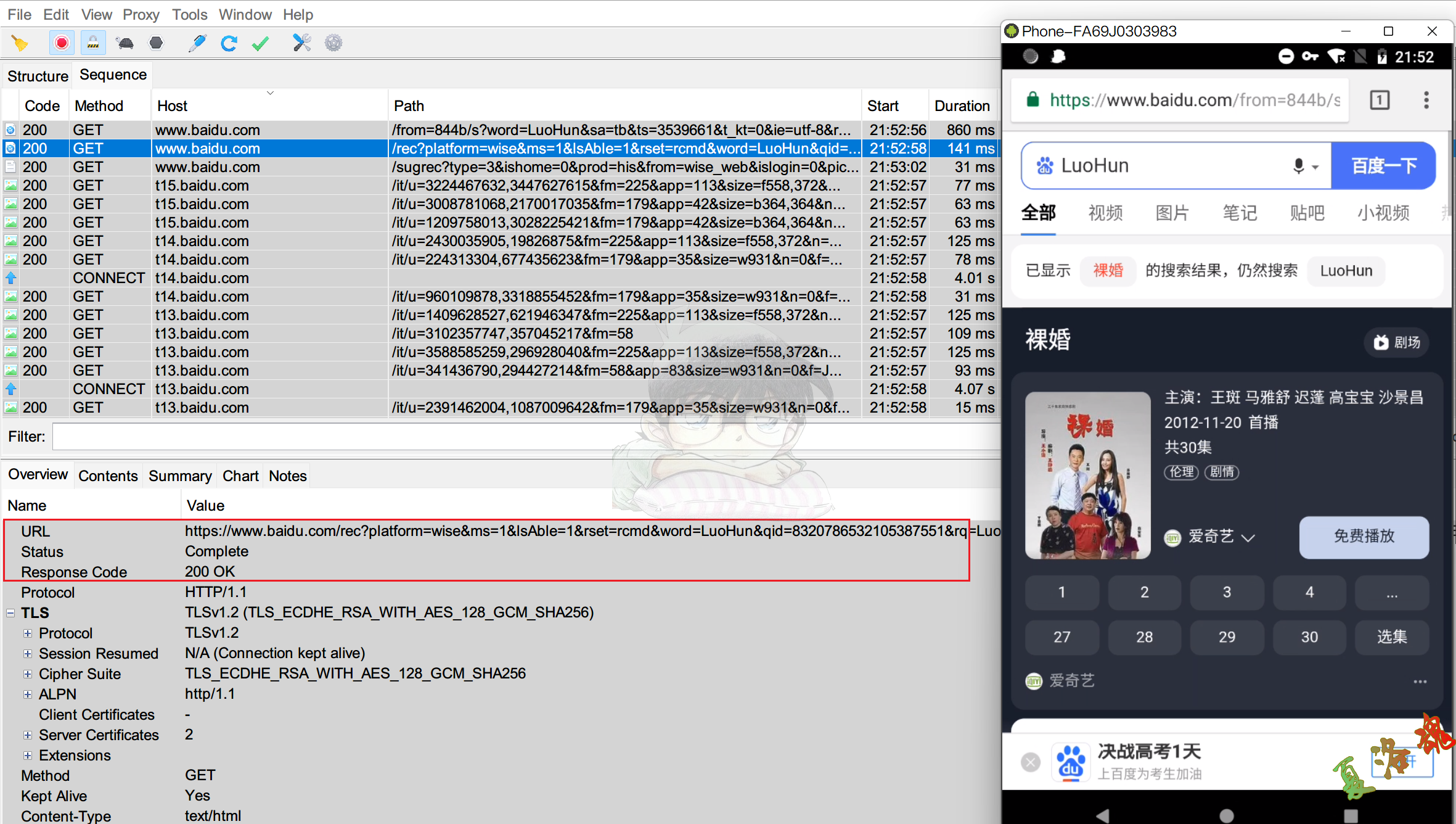
PC端使用Charles,手机端使用Postern(Socks模式),PC端和手机端在同一局域网环境下且Charles证书已安装到手机系统分区中,手机端使用浏览器访问百度进行测试.
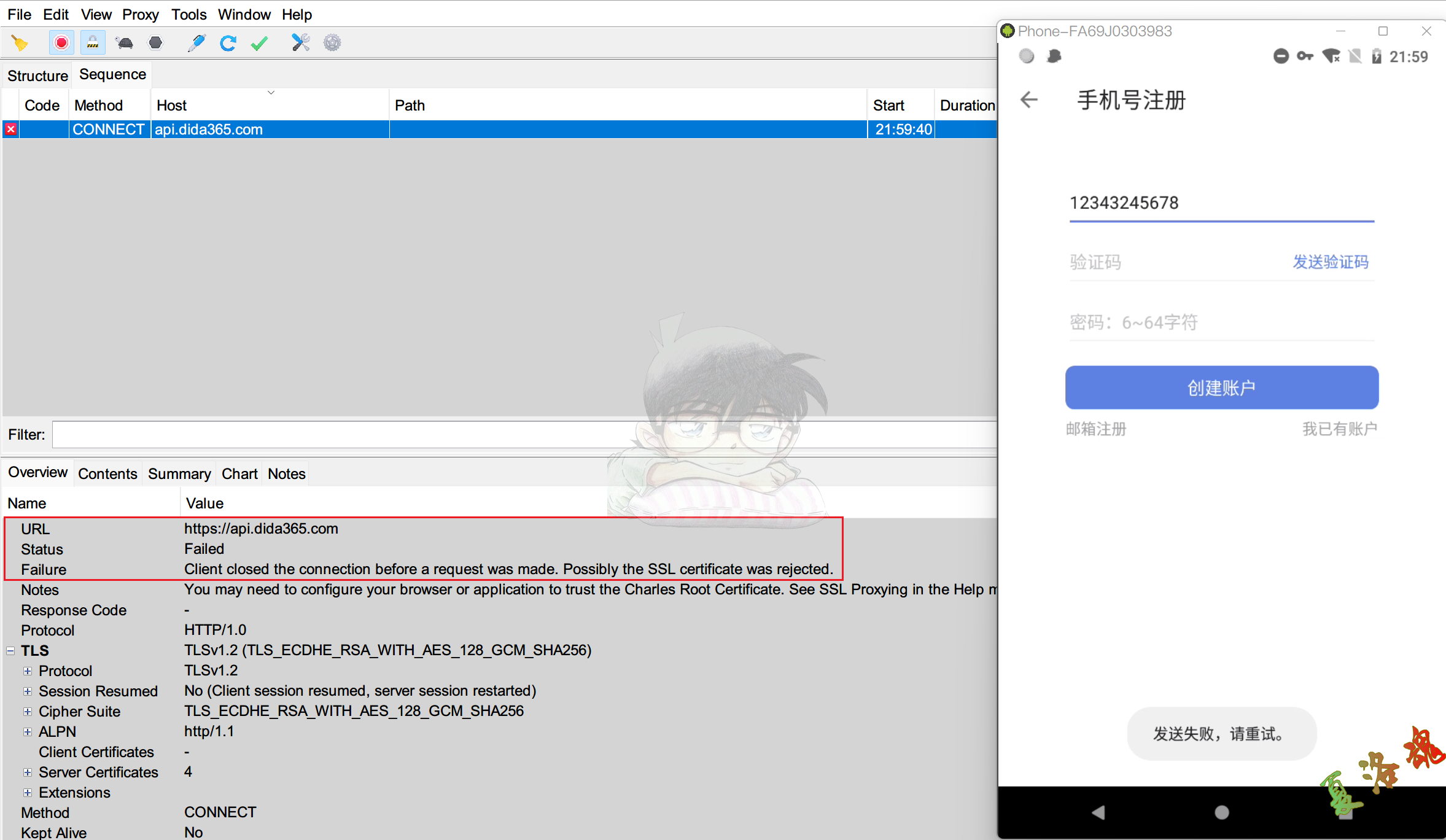
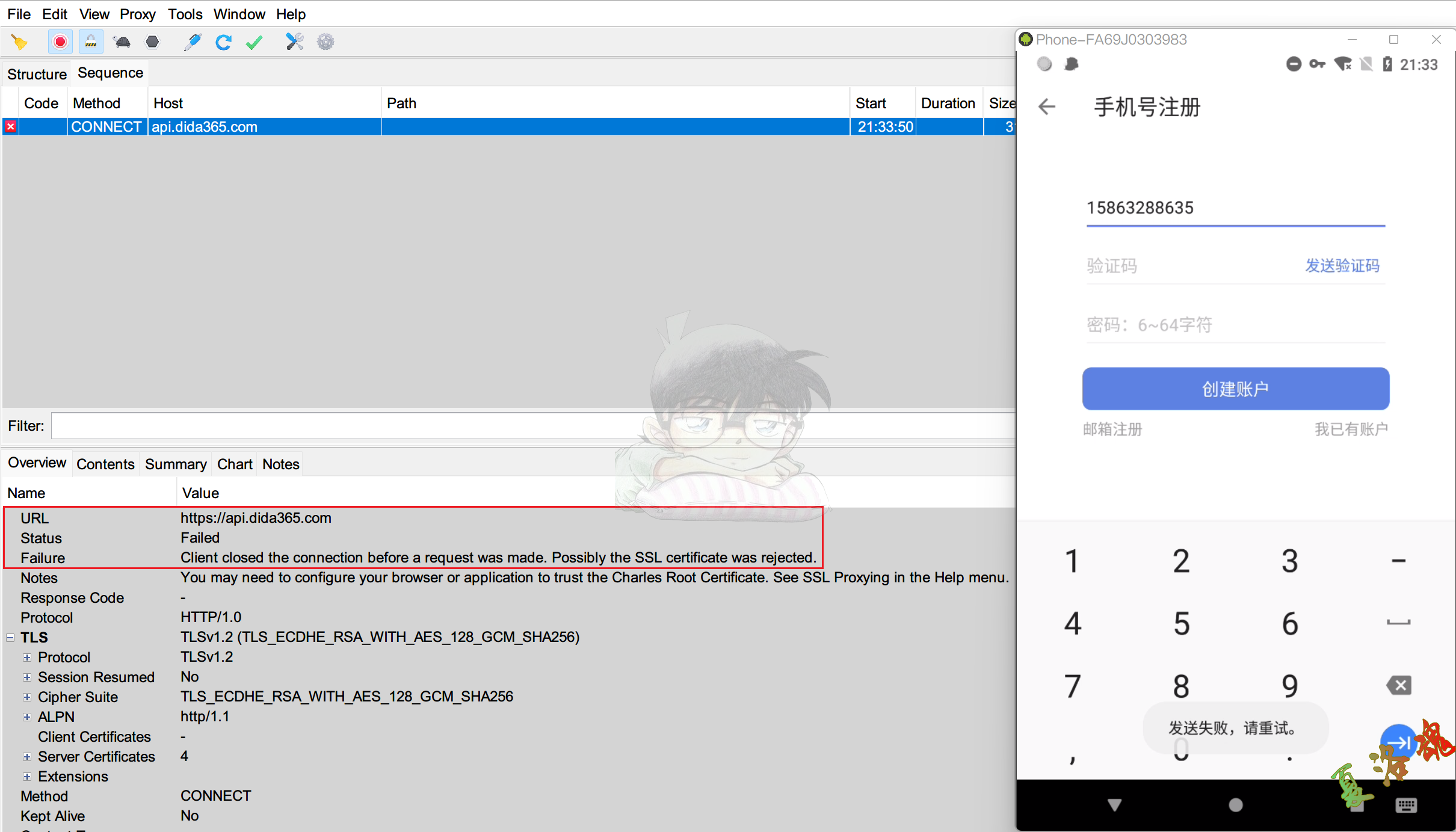
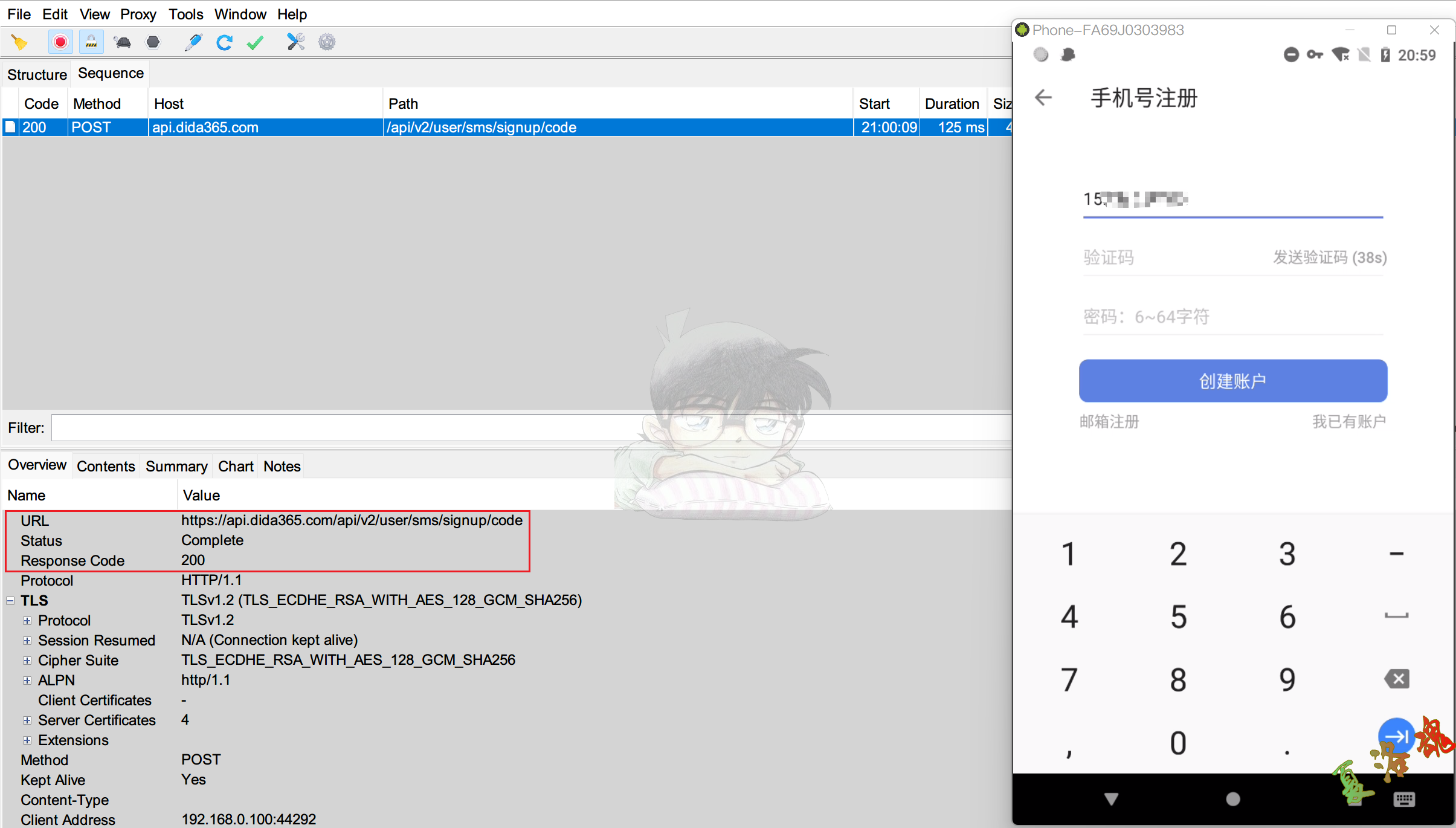
打开案例App,测试通过手机号注册发送验证码流程.
经过多次测试,发现某些网址的抓包结果总是提示"Client closed the connection before a request was made. Possibly the SSL certificate was rejected.",也就说客户端主动停止与服务器的连接,App使用了证书绑定技术.
解决方案
由于上面这种方式对证书验证的代码是写在App内部,所以我们可以通过Hook的方式让执行证书绑定的函数失效.而Hook可行的前提是能够确定证书绑定的函数,此时需要对不同网络框架中证书绑定相关的代码有一定了解.例如,App使用okhttp3网络框架进行证书绑定,那么使用的证书绑定类总是CertificatePinner类,此时Hook的目标就是CertificatePinner类中的函数;App使用TrustManager类完成证书的绑定,那么Hook的目标就是TrustManager类中的证书绑定函数.
1
2
3
4
5
6
OkHttpClient client = new OkHttpClient . Builder ()
//完成证书绑定
. certificatePinner ( new CertificatePinner . Builder ()
. add ( "test.com" , "sha512/14cf3DRF..." )
. build ())
. build ();
前人研究
Android世界中有很多的网络框架,如果对每个网络框架都进行证书绑定函数的确定,工作量很大.但幸运的是,前人已经完成了很多种网络框架的证书绑定函数的收集工作,可供我们参考.
Objection
考虑到App在启动之前就已经完成了证书绑定,所以我们首先要确保App进程完全关闭,然后利用Objection的-s/–start-command参数达到命令在应用启动之前就执行的效果.
1
objection.exe -g cn.ticktick.task explore -s "android sslpinning disable"
从上面结果中可以看到依旧是失败,出现这个问题可能是Objection工具未集成足够多的网络框架证书绑定函数而造成的.
DroidSSLUnpinning
https://github.com/WooyunDota/DroidSSLUnpinning/blob/master/ObjectionUnpinningPlus/hooks.js
1
frida -U -f cn.ticktick.task -l .\hooks.js --no-pause
okhttp-sslunpinning
https://github.com/bxl0608/okhttp-sslunpinning
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
var classesNames = new Array ()
var OkhttpClientClassName = ""
var CertificatePinnerClassName = ""
var prefix = ""
function initConsole (){
var Color = { RESET : " \x1b [39;49;00m" , Black : "0;01" , Blue : "4;01" , Cyan : "6;01" , Gray : "7;11" , "Green" : "2;01" , Purple : "5;01" , Yellow : "3;01" , Red : "1;01" }
var LightColor = { RESET : " \x1b [39;49;00m" , Black : "0;11" , Blue : "4;11" , Cyan : "6;11" , Gray : "7;01" , "Green" : "2;11" , Purple : "5;11" , Red : "1;11" , Yellow : "3;11" }
var colorPrefix = ' \x1b [3'
var colorSuffix = 'm'
Object . keys ( Color ) . forEach ( function ( c ){
if ( c == "RESET" )
return
console [ c ] = function ( message ){
console . log ( colorPrefix + Color [ c ] + colorSuffix + message + Color . RESET )
}
console [ "Light" + c ] = function ( message ){
console . log ( colorPrefix + LightColor [ c ] + colorSuffix + message + Color . RESET )
}
})
}
function loadOkhttpClient (){
Java . perform ( function (){
try {
Java . use ( "okhttp3.OkHttpClient" )
} catch ( e ){
// console . error ( e )
}
})
}
function loadClasses (){
Java . perform ( function (){
Java . enumerateLoadedClasses ({
onMatch : function ( clsName , handle ){
classesNames . push ( clsName )
},
onComplete : function (){
console . Green ( "Search Class Completed!" )
}
})
})
}
function findOkhttpClass (){
Java . perform ( function (){
var Modifier = Java . use ( "java.lang.reflect.Modifier" )
function isOkhttpClient ( clsName ){
if ( clsName . split ( '.' ) . length != 2 ){
return false ;
}
try {
var cls = Java . use ( clsName )
var interfaces = cls . class . getInterfaces ()
const count = interfaces . length
if ( count < 2 ){
return false
}
var flag = false
for ( var i = 0 ; i < count ; i ++ ){
var interface_ = interfaces [ i ]
var interface_name = interface_ . getName ()
if ( interface_name . indexOf ( "Cloneable" ) > 0 ){
flag = true
} else {
if ( interface_name . indexOf ( "$" ) <= 0 ){
return false
}
}
}
if ( ! flag ) return false ;
if ( cls . class . getDeclaredClasses () . length < 1 ){
return false
}
if ( cls . class . getSuperclass () . getName () != 'java.lang.Object' ){
return false
}
} catch ( e ){
return false
}
return true ;
}
function isCertificatePinner ( clsName , prefix ){
if ( ! clsName . startsWith ( prefix )){
return false
}
if ( clsName . indexOf ( "$" ) > 0 ){
return false
}
if ( clsName . split ( '.' ) . length != 2 ){
return false ;
}
var cls = Java . use ( clsName )
if ( cls . class . isInterface ()){
return false
}
if ( cls . class . getInterfaces () . length > 0 ){
return false
}
if ( cls . class . getDeclaredClasses () . length < 1 ){
return false
}
if ( cls . class . getSuperclass () . getName () != "java.lang.Object" ){
return false
}
if ( ! Modifier . isFinal ( cls . class . getModifiers ())){
return false
}
var flag = false
var methods = cls . class . getDeclaredMethods ()
for ( var i = 0 ; i < methods . length ; i ++ ){
var method = methods [ i ]
if ( method . getParameterCount () < 1 ){
continue
}
if ( method . getParameterTypes ()[ 0 ] . getName () == "java.security.cert.Certificate" ){
flag = true
break
}
}
if ( ! flag ) return false
flag = false
var fields = cls . class . getDeclaredFields ()
for ( var k = 0 ; k < fields . length ; k ++ ){
var field = fields [ k ];
if ( field . getType () . getName () == "java.util.Set" ){
flag = true
break
}
}
if ( ! flag ) return false
return true
}
for ( var i = 0 ; i < classesNames . length ; i ++ ){
if ( isOkhttpClient ( classesNames [ i ])){
OkhttpClientClassName = classesNames [ i ]
var prefix = classesNames [ i ] . split ( '.' )[ 0 ] + '.'
}
}
for ( var i = 0 ; i < classesNames . length ; i ++ ){
if ( isCertificatePinner ( classesNames [ i ], prefix )){
CertificatePinnerClassName = classesNames [ i ]
}
}
var printOut
if ( OkhttpClientClassName == "" || CertificatePinnerClassName == "" || prefix == "" ){
printOut = console . Red
printOut ( "Can't find the okhttp class" )
} else {
printOut = console . Green
}
printOut ( "Found Class: " + classesNames . length )
printOut ( "Okhttp's package prefix: " + prefix )
printOut ( "Found the OkhttpClient: " + OkhttpClientClassName )
printOut ( "Found the OkhttpCertificatePinner: " + CertificatePinnerClassName )
})
}
function hook (){
Java . perform ( function (){
var Modifier = Java . use ( "java.lang.reflect.Modifier" )
// TrustAllManager
var TrustAllManagerClass = Java . registerClass ({
name : "TrustAllManager" ,
implements :[ Java . use ( "javax.net.ssl.X509TrustManager" )],
methods : {
checkClientTrusted ( chain , authType ) {
console . Cyan ( "checkClientTrusted Called!!" )
},
checkServerTrusted ( chain , authType ) {
console . Cyan ( "checkServerTrusted Called!!" )
},
getAcceptedIssuers () {
return [];
},
}
})
var trustAllManagerHandle = TrustAllManagerClass .$ new ()
var sslContext = Java . use ( "javax.net.ssl.SSLContext" ) . getInstance ( "TLS" )
sslContext . init ( null , Java . array ( "Ljavax.net.ssl.X509TrustManager;" ,[ trustAllManagerHandle ]), null )
var sslSocketFactory = sslContext . getSocketFactory ()
// HostnameVerify
var MyHostnameVerify = Java . registerClass ({
name : "MyHostnameVerify" ,
implements :[ Java . use ( "javax.net.ssl.HostnameVerifier" )],
methods : {
verify ( hostname , session ){
console . log ( hostname )
return true
}
}
})
var myHostnameVerifyHandle = MyHostnameVerify .$ new ()
var internalOkhttpClientClasses = Java . use ( OkhttpClientClassName ) . class . getDeclaredClasses ()
internalOkhttpClientClasses . forEach ( function ( internalClass ) {
var methods = internalClass . getDeclaredMethods ()
methods . forEach ( function ( method ) {
if ( method . getParameterCount () < 1 ){
return
}
var firstParameterTypeName = method . getParameterTypes ()[ 0 ] . getName ()
if ( firstParameterTypeName == "javax.net.ssl.SSLSocketFactory" ){
var Builder = Java . use ( internalClass . getName ())
var sslSocketFacotryMethodName = method . getName ()
Builder [ sslSocketFacotryMethodName ] . overloads . forEach ( function ( overload ){
overload . implementation = function ( SSLSocketFactory ){
arguments [ 0 ] = sslSocketFactory
return this [ sslSocketFacotryMethodName ] . apply ( this , arguments )
}
console . Blue ( sslSocketFacotryMethodName + " Hooked!" )
});
}
if ( firstParameterTypeName == "javax.net.ssl.HostnameVerifier" ){
var Builder = Java . use ( internalClass . getName ())
var hostnameVerifierMethodName = method . getName ()
Builder [ hostnameVerifierMethodName ] . overloads . forEach ( function ( overload ){
overload . implementation = function ( hostnameVerifier ){
arguments [ 0 ] = myHostnameVerifyHandle
return this [ hostnameVerifierMethodName ] . apply ( this , arguments )
}
console . Yellow ( hostnameVerifierMethodName + " Hooked!" )
});
}
if ( firstParameterTypeName == CertificatePinnerClassName ){
var Builder = Java . use ( internalClass . getName ())
var certificatePinnerMethodName = method . getName ()
Builder [ certificatePinnerMethodName ] . overloads . forEach ( function ( overload ){
overload . implementation = function ( certificatePinner ){
return Java . retain ( this )
}
console . Purple ( certificatePinnerMethodName + " Hooked!" )
});
}
})
});
var CertificatePinnerClass = Java . use ( CertificatePinnerClassName )
var methods = CertificatePinnerClass . class . getDeclaredMethods ()
methods . forEach ( function ( method ){
if ( method . getReturnType () . getName () == 'void' ){
var methodName = method . getName ()
console . Cyan ( methodName + " Hooked!" )
CertificatePinnerClass [ methodName ] . overloads . forEach ( function ( overload ){
if ( overload . returnType . name == 'V' ){
overload . implementation = function (){
console . Cyan ( "certificatePinner check called!" )
}
}
})
}
})
})
}
function main (){
initConsole ()
loadOkhttpClient ()
loadClasses ()
findOkhttpClass ()
hook ()
}
setImmediate ( main )
这个主要针对被混淆过的okhttp框架,恰好测试的案例的okhttp框架被混淆过.
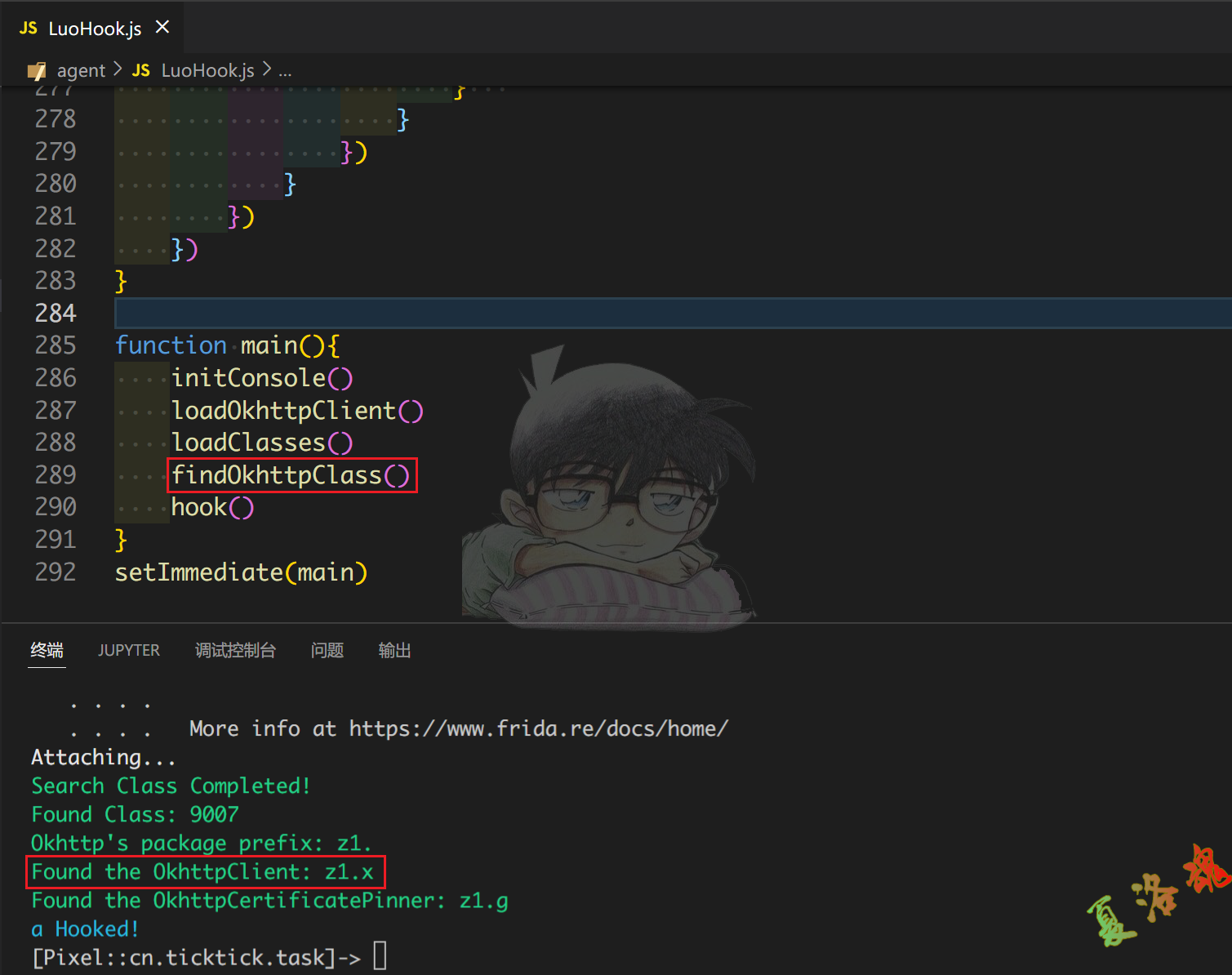
先使用attach模式,找到经过混淆的OkhttpClient类.
修改loadOkhttpClient中加载的类为上述找到的经过混淆的类.
使用Frida进行Hook,以spawn模式来启动Apk即可.
结论
经过测试,前两种方案对目前测试的案例是不行的,第3种方案可以.
常规思路
在经过上述前人总结的2种方案都失败后,可以得到一个结论:App被混淆了.这种情况下,有两种思路可以借鉴:
使用Objection对所有Http字符串相关类进行Hook,定位关键的证书绑定函数.
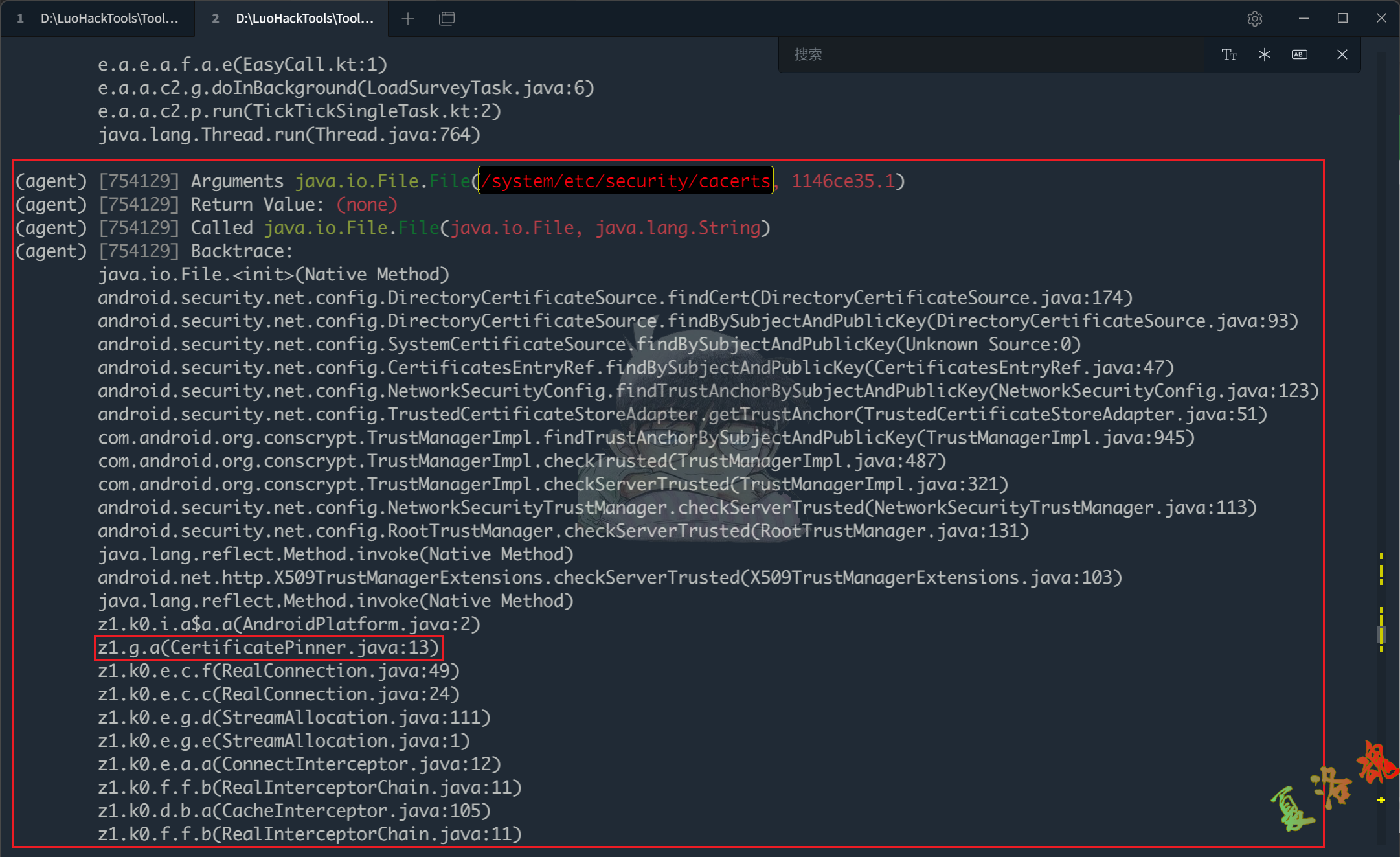
考虑到App在验证证书时一定会打开证书文件判断是否是App自身信任的,因此一定会使用File类的构造函数打开证书文件获得文件句柄,故我们可以Hook File类的构造函数,即File$init函数.(推荐)
这里我们使用第2种方案,确保App完全关闭,然后利用Objection完成注入.需要注意的是,在终端中"$“是特殊字符,需要进行转义.
1
objection.exe -g cn.ticktick.task explore -s "android hooking watch class_method java.io.File.'$'init --dump-args --dump-backtrace --dump-return"
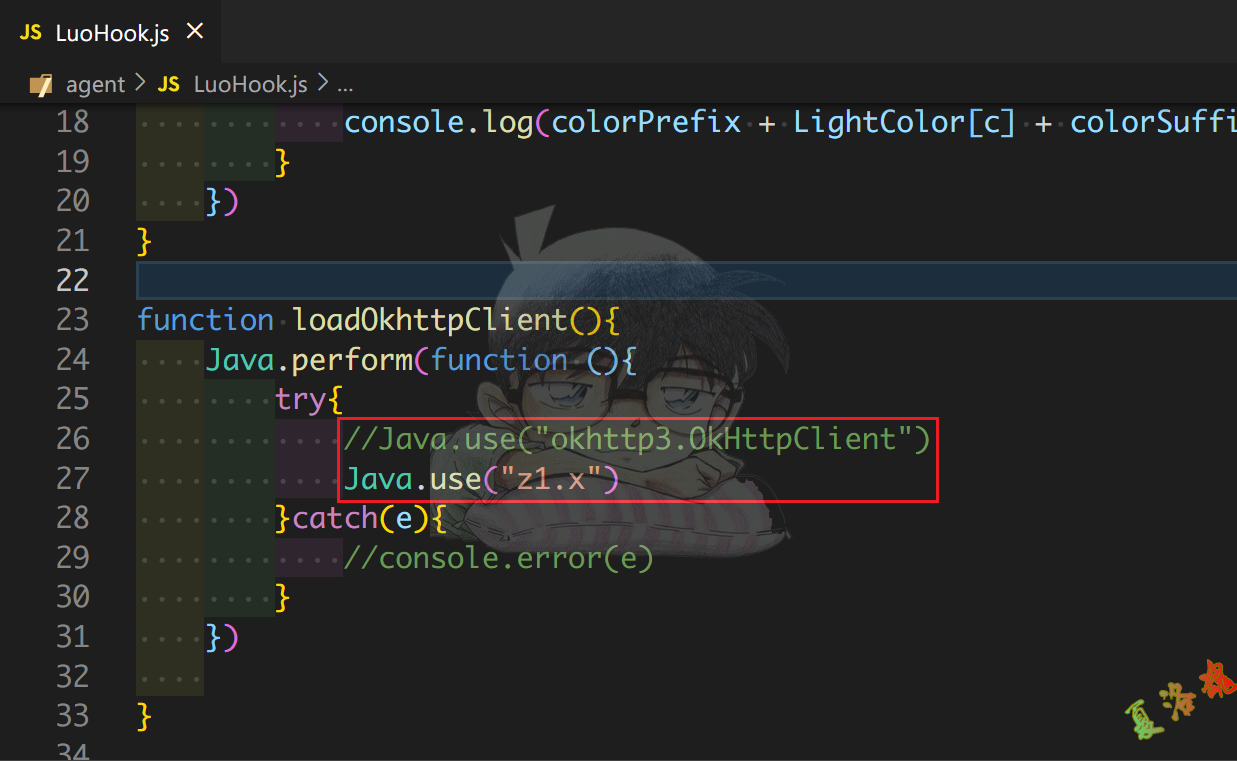
接下来以/system/etc/security/cacerts这个系统存放证书的路径为关键词在终端进行搜索,就会发现有一个栈的信息中存在非常明显的CertificatePinner.java文件名信息,因此可以判定函数z1.g.a()就是对应的完成证书绑定的函数.
Hook脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
function killCertificatePinner (){
Java . perform ( function (){
console . log ( "Beginning killCertificatePinner !..." )
Java . use ( "z1.g" ). a . implementation = function ( str , list ){
console . log ( "called z1.g.a ~" )
return ;
}
})
}
function main (){
killCertificatePinner ();
}
setImmediate ( main );
参考链接
<安卓Frida逆向与抓包实战>